Easy Challenge Room: Lo-Fi on TryHackMe – A Simple Room for Beginners
Welcome to today’s walkthrough of the Lo-Fi challenge room on TryHackMe! This room is one of the easiest challenges I’ve encountered, making it perfect for beginners who are getting started with web application security.
If you’re familiar with the basics of web vulnerabilities like Directory Traversal and Local File Inclusion (LFI), you’ll find this room straightforward. The challenge focuses on these concepts and helps you build practical knowledge in a hands-on environment.
By the end of this room, you’ll strengthen your understanding of how these vulnerabilities work and how to exploit them safely.
Whether you’re just starting your cybersecurity journey or brushing up on your skills, Lo-Fi on TryHackMe is an excellent place to practice and learn. Ready to dive in? Let’s go!
First start with the nmap scan.
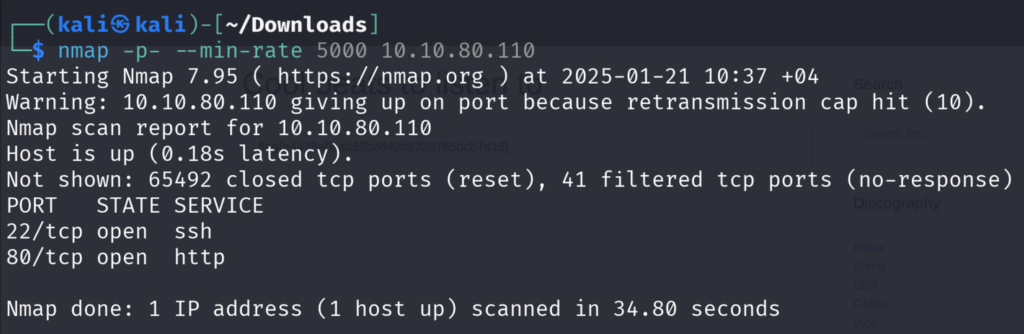
The Description tells us that there is a flag in the root of the filesystem. and the similar content in Tryhackme are Directory Traversal and File Inclusion. So, I immediately went to the web application and look for the endpoints.
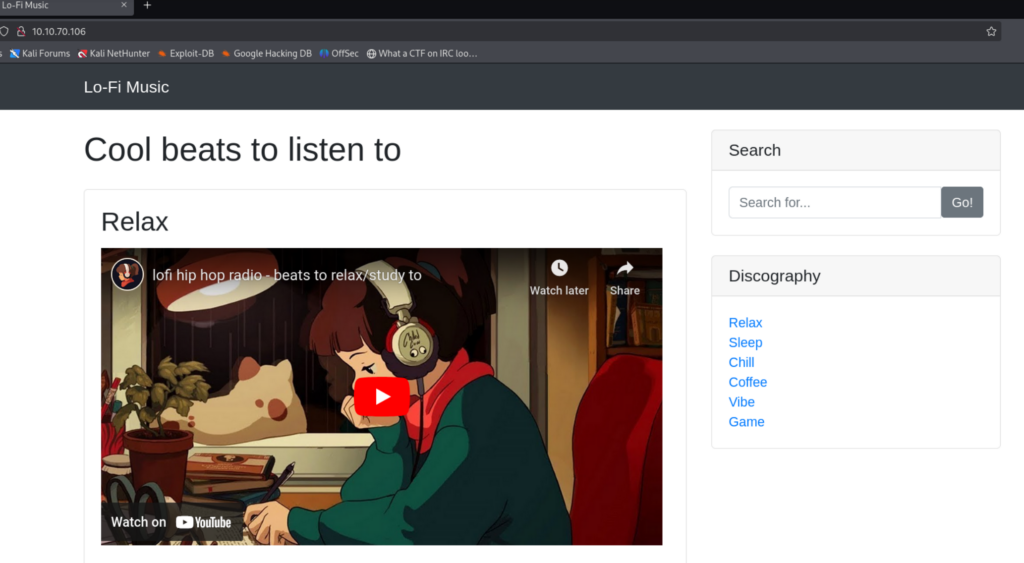
If you click on any one of the endpoints you will come across a php page related to the discography. So, click on the relax link.
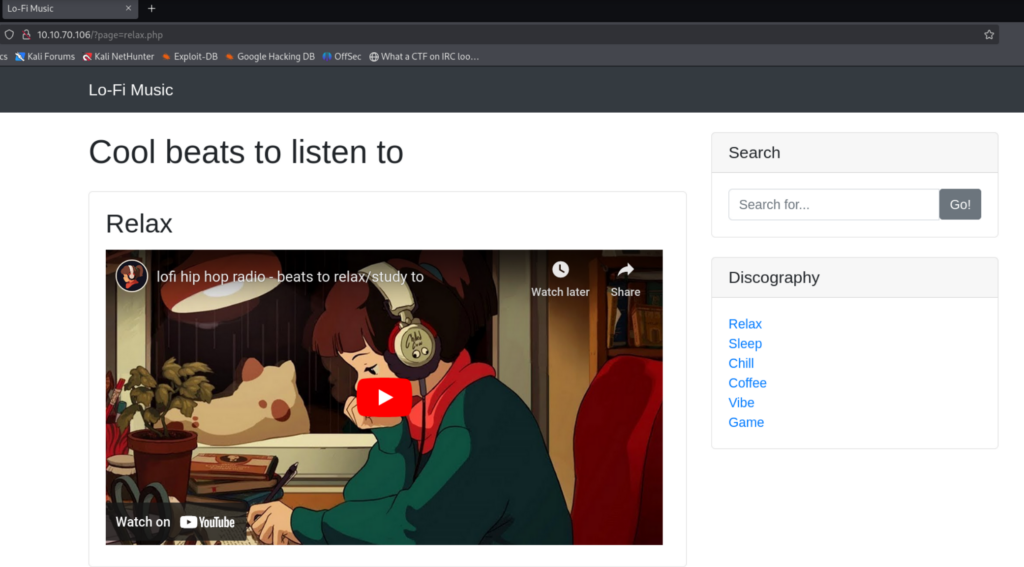
The URL shows that it accepts a query string. Let’s replace relax.php with the directory traversal sequences with passwd file to check if it is vulnerable to Local File Inclusion.
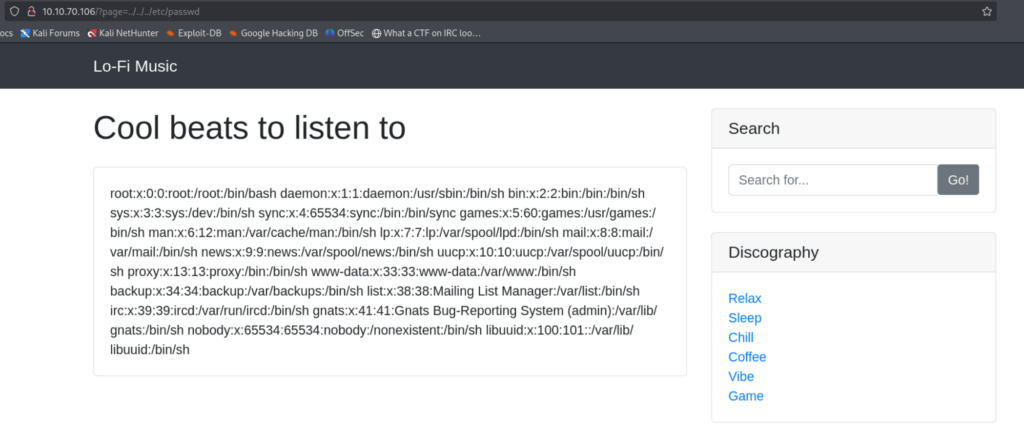
Yesss, We can see that we are able to see the passwd file locally. The Lab has already told us that the flag is at the root of the filesystem.
So We will do the traversal sequences but with flag.txt
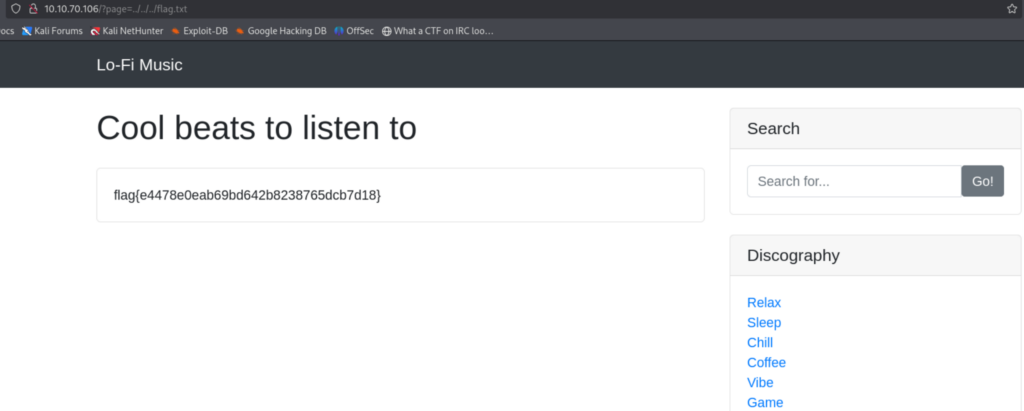
Viola, Here is your go you see the flag locally so you can just copy and paste from the webpage.
A huge shoutout to cmnatic. He is an Amazing Guy who has created all sorts of rooms in TryHackMe, do check out the created rooms of cmnatic.
That’s it from my side. Peace.



